Trust Every Connection. Even the Autonomous Ones.
Riptides is the non-human identity fabric for your workloads and AI agents.
Stop scattering secrets,
start trusting identities.
Unify and secure secrets across your entire stack.
End Non-Human Credential Sprawl
Secure connections with real non-human identities.
Issue and rotate short-lived identities automatically.
Move access control from the network to the workloads.
Use identity to authenticate and encrypt every connection.
Monitor and audit all workload interactions for compliance.
Eliminate Human Error
from Secret Management
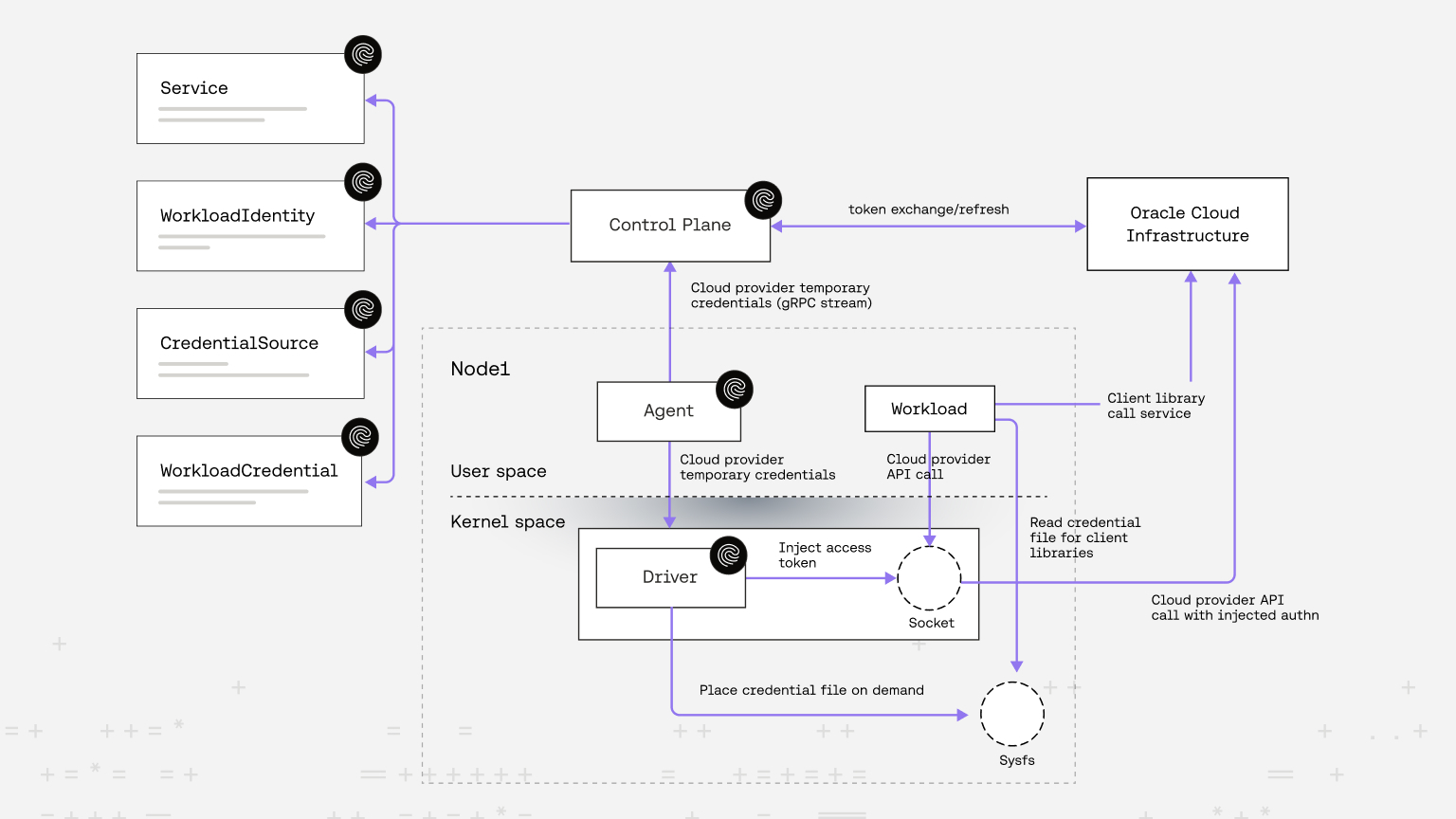
Enforce and propagate real workload identities at the OS kernel level.
Skip secrets and code changes – give every workload a real identity.
Make the network stack simpler with kernel-level enforcement.
Automate mutual TLS without touching application code.
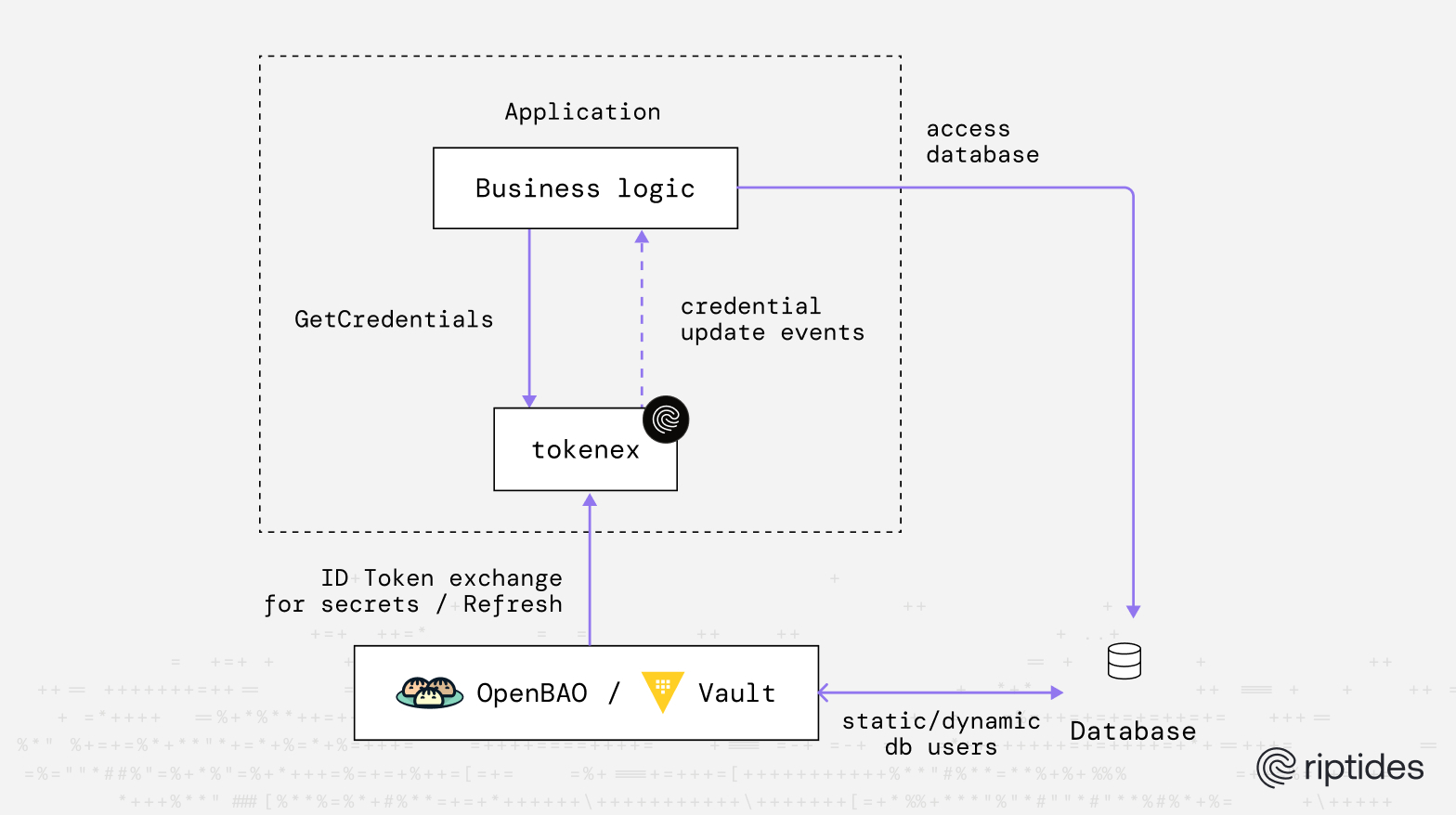
Exchange trusted identities for just-in-time third-party credentials.
Let AI Agents Act with Confidence
Plug identity and access control directly into your agent infrastructure.
Issue trusted, verifiable identities to every AI agent.
Ensure every agent-to-agent connection is trusted and secure.
Control what agents can do as they move and evolve.
Automatically log and monitor every action an agent takes.
Features For
Security Teams
Riptides puts access control in the hands of platform and security teams — and takes care of the rest.
Secret Detection
Monitor network traffic to detect secrets in transit.


Credential Inventory
Maintain a real-time inventory of all your non-human credentials.
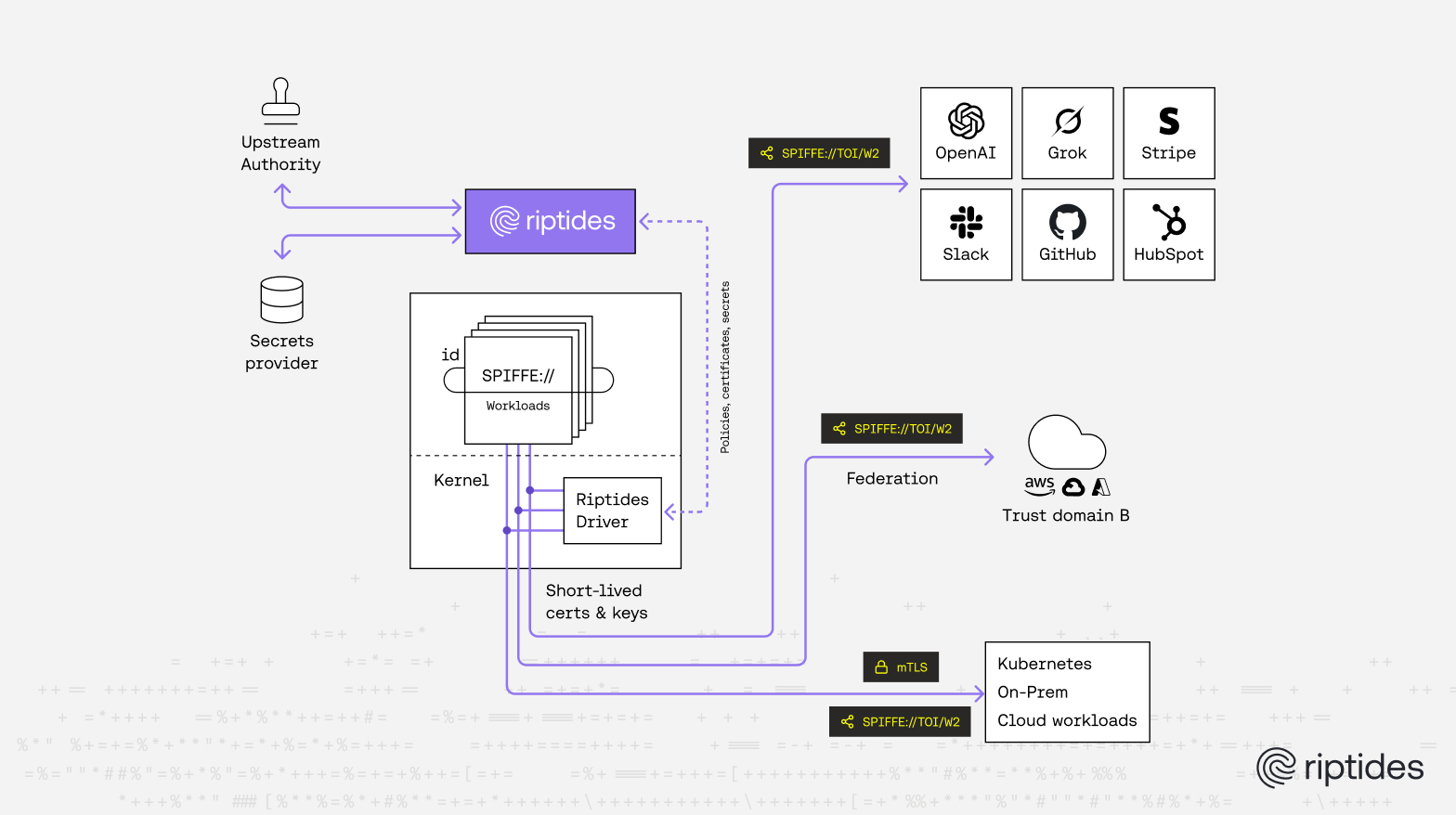
Trust Federation
Establish federated trust between systems through SPIFFE trust domains.

Credential Exchange
Automatically exchange identities for third-party credentials

Runtime Security
Enforce process-level access control to block sophisticated malware.


Standards-Based
Integrate seamlessly with your existing network and security infrastructure.
Integrations
Connect with your existing infrastructure and tools.
Kubernetes
Build identities by relying on Kubernetes metadata.
SPIFFE
Integrate with existing systems using SPIFFE and standard SVIDs.
OpenAI
Securely inject API keys into OpenAI agents at runtime.
Grok
Provide Grok agents with API keys without exposing secrets.
AWS
Federate trust across AWS with IAM Roles Anywhere.
Google Cloud
Give workloads access to Google Cloud using Workload Identity Federation
Ready to replace secrets
with trusted identities?
Build with trust at the core.

Latest Riptides News
Deep dives on secure identity, AI agent infrastructure, and what's next for workload-to-workload trust.
Frequently Asked Questions
Who is Riptides for?
Riptides is built for security engineers, platform and infrastructure teams who want to secure workload-to-workload communication across dynamic, cloud-native, and AI-native environments by relying on true non-human identities and without managing a mess of credentials.
How is Riptides different from a secrets manager?
Riptides assigns and distributes real non-human identities to workloads and agents, then uses those identities directly to secure connections. In cases where a secret is still needed, like accessing a third-party API, Riptides acts similarly to a secrets manager, but it issues those secrets automatically based on the requesting identity, with no manual handling.
How is Riptides different from SPIRE?
Riptides also relies on the SPIFFE standard for identity, but enforces identities at the kernel level, not in user space. This allows us to assign and propagate identities transparently, with no changes required to application code. Unlike SPIRE, Riptides supports automatic secret management for third-party integrations based on identity, and includes dashboards for credential inventory, access visibility, and compliance reporting.
What makes kernel-level enforcement better?
Enforcing access at the kernel level means identities are tied directly to running processes, not to network locations or application logic. It’s fully independent of both the applications running on the node and the underlying network stack. This helps prevent identity spoofing and allows Riptides to block malicious connections, even if they originate from the same node or pod using valid credentials.
Is Riptides compatible with my existing infrastructure?
Yes. Riptides integrates with Kubernetes and container platforms to collect workload metadata, allowing you to write policies against familiar primitives like pods, namespaces, and service accounts, not just low-level Linux constructs. It supports open standards like SPIFFE and TLS, and operates independently of the underlying network stack. Riptides can also be introduced gradually, making it easy to adopt without requiring a full platform overhaul.
Do I need to change my application code?
No. Riptides works below the application layer — no SDKs, no code changes, and no TLS boilerplate required.
Will Riptides be open source?
Yes. We plan to open source the core of Riptides — including the kernel module that powers identity enforcement. We believe open sourcing this foundation increases transparency, builds trust with the community, and makes it easier for teams to audit and adopt the technology with confidence.
Does Riptides store secrets or credentials outside my environment?
No. The Riptides control plane never stores your secrets or credentials. Any component responsible for handling secrets, including issuing identities or managing third-party credentials, is always deployed within your environment, ensuring sensitive data never leaves your trust boundary.
Is Riptides a cloud-based service, or does it run inside my infrastructure?
Riptides can run fully within your infrastructure, or in a hybrid model where the control plane is delivered as a managed service while enforcement and identity issuance happen locally. Even in the hybrid model, secrets and credentials are never stored in the managed service. All sensitive operations stay within your environment.