The Safest Secret Is the One That Doesn’t Exist
In our cloud-native world, secrets are liabilities: like API keys exposed in logs, vaulted credentials that never get revoked, or old tokens lying in backups. Each one is a ticking time bomb, waiting to be exploited.
As Felix Gaehtgens recently argued, the biggest challenge isn’t just storing secrets, but the bootstrap problem: how do you securely give a workload its first credential without already having one in place? SPIFFE’s vision - eliminating credential chaos by issuing short-lived, verifiable identities at runtime - is the right answer to that decades-old chicken-and-egg dilemma.
At Riptides, we share this vision. But we also believe that to make workload identity truly universal, it needs to be seamless, short-lived or ephemeral, automatic, and anchored where it can’t be bypassed: in the kernel.
1. The Hidden Cost of Credentials
Every secret comes with baggage:
- Creation & injection into environment variables, CI pipelines, metadata services.
- Storage in vaults or config files.
- Rotation or revocation a process rife with human error.
- Attack surface across logs, backups, staging images, CI job definitions - the list is long.
As Felix noted, cloud IAM roles and service accounts work well within their boundaries. But outside those silos, teams fall back to vaults and static credentials, multiplying risk with every workload.
NHIM tools help organize the chaos, but they don’t eliminate it. Riptides flips the script: no secrets, no fragility, no leaks, just workload identity, reimagined in the kernel.
2. Cryptographic Trust Rooted in Identity, Not Treasures
Instead of relying on “what you hold” (a password, a token), we look to “who you are” - and prove it continuously.
- SPIFFE IDs: Cryptographically rooted identities issued at runtime.
- Kernel-level attestation: Continuous proof of identity based on how and where the workload is running.
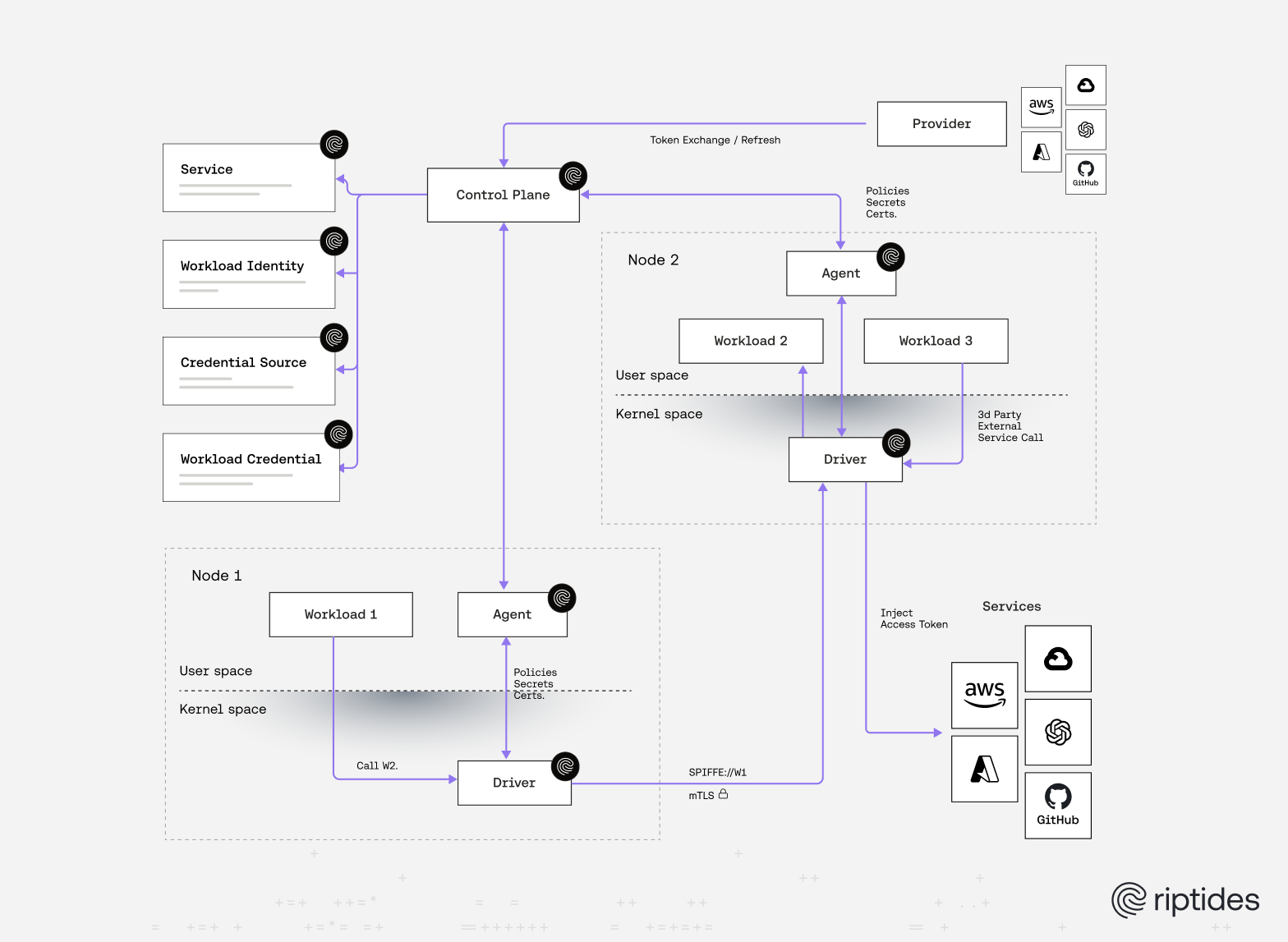
No vault. No tokens. Just cryptographic certainty tied directly to runtime provenance and purpose. Just workload identity reimagined at the kernel level.
3. From SPIFFE to Seamless Adoption
SPIFFE provides the standard foundation: short-lived SVIDs, attestation, and universal trust. But in practice, most deployments bolt identity onto sidecars and proxies. This adds complexity, weakens trust boundaries, and creates friction that slows mass adoption.
In our post Rethinking Workload Identity at the Kernel Level, we argue that identity must be:
- Kernel-native - bound directly to individual process instances.
- Ephemeral - spun up with the workload and gone when it terminates.
- Process-isolated - ensuring only the right code path receives identity.
This makes workload identity invisible to developers, operationally effortless for teams, and universally enforceable.
4. A Foundation for the Post-Credential Era
SPIFFE has shown us the way: workload identity without static credentials is possible. The next step is making it automatic, seamless, and tied to the process itself - so that it scales across clouds, VMs, bare metal, and edge environments without operational burden.
Because in the post-credential era, identity isn’t something you distribute or rotate. It’s something you prove - cryptographically, continuously, and without secrets.
If you enjoyed this post, follow us on LinkedIn and X for more updates. If you’d like to see Riptides in action, get in touch with us for a demo.
Ready to replace secrets
with trusted identities?
Build with trust at the core.