Securing Workloads with Kernel Telemetry and Metrics
In modern infrastructure, workloads-not humans-make most of the decisions and connections. They spin up services, authenticate peers, and communicate across nodes faster than any human operator ever could. Yet, to secure and verify these interactions, we need visibility deep enough to understand intent, not just traffic. At Riptides, this journey started in the Linux kernel-with tracepoints.
This post recaps our path from breakpoints to production ready Prometheus metrics and shows how kernel-level telemetry empowers our non-human identity platform with unmatched context and trust.
From Debugging to Tracing: Listening to the Kernel
Our journey began where most kernel work does: debugging. Traditional breakpoints offer a glimpse into execution but halt progress-fine for development, not for real-time systems. In our first post, we moved from breakpoints to tracepoints, opening a window into kernel events without blocking the system.
Tracepoints are efficient, built-in hooks in the Linux kernel. They let us observe what's happening-packet reception, syscalls, context switches-without modifying the code or stopping execution. For observability and security alike, that non-intrusive visibility is gold.

Surfacing Events: Tracepoints to User-Space Metrics
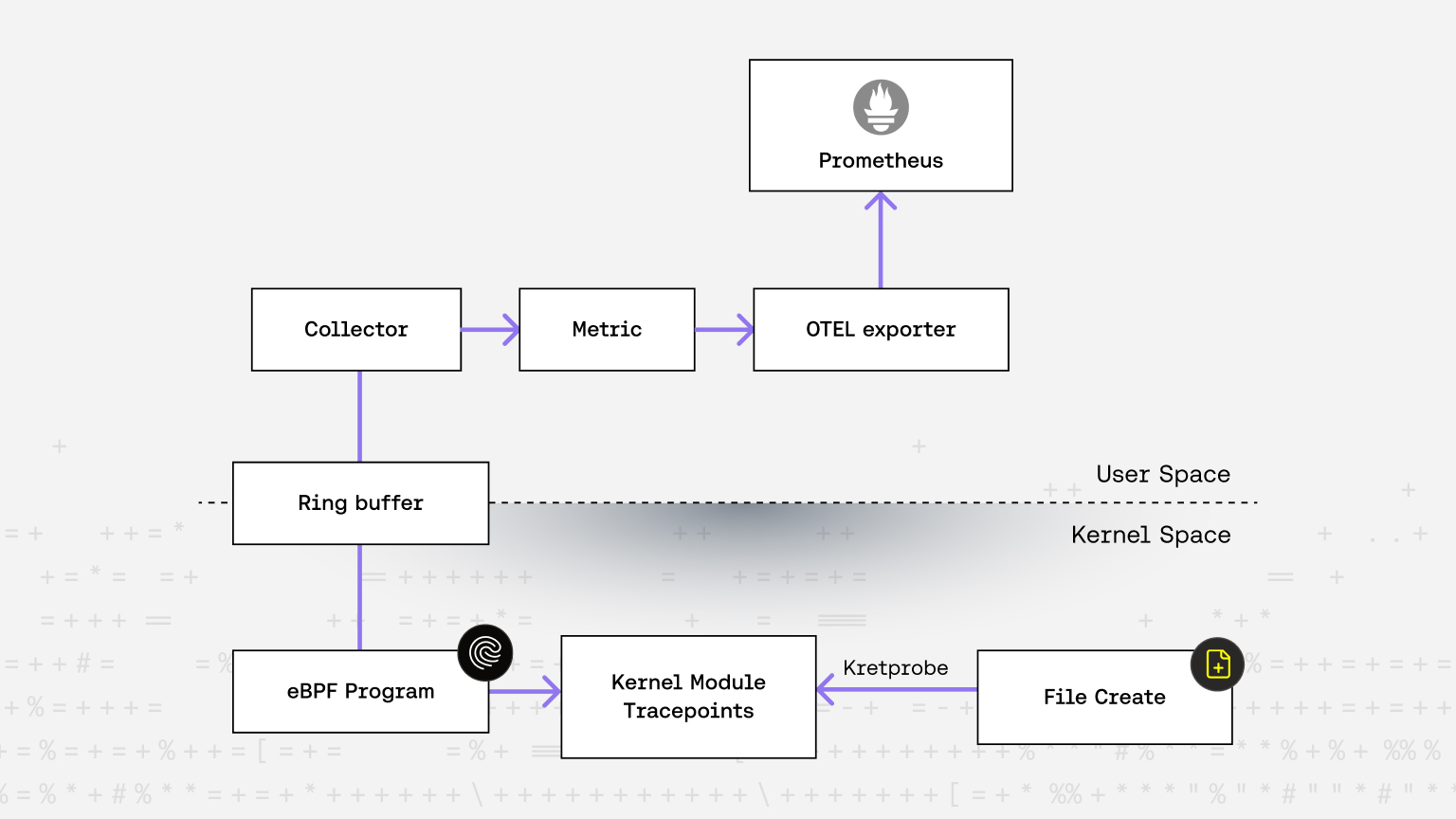
Tracepoints give us low level visibility, but events alone isn’t insight. In our second post, we detailed how we transform tracepoint events into structured telemetry consumable by our userspace systems.
The key is efficient transport. We use ringbuf (not perfbuf) for minimal overhead and latency. We write custom kernel modules to handle filtering, sampling, and formatting near the source. This avoids swamping userspace with noise and allows us to focus on high value signals-like syscall patterns, packet anomalies, or handshake timelines.

From Kernel Events to Prometheus Metrics
With structured events flowing into user-space, the next step is surfacing them to the broader observability ecosystem. In our third post, we connected our kernel events to Prometheus metrics.
Why Prometheus? Because it's the lingua franca of observability. Engineers and security teams alike already use it. By exposing metrics from kernelspace (e.g., handshake latencies, dropped packets, authentication attempts), we enrich dashboards and alerts with context that typically lives far beneath the surface.
Instead of just "500 errors increased," we can say, "TLS handshake failed for pod A to B due to invalid identity, traced to ksys_read syscall path and confirmed by dropped SYN-ACK in tcp_retransmit_skb."
This is not just observability. It's forensics in real time.
Beyond the Usual Suspects: Telemetry as a Security Primitive
While most telemetry focuses on CPU, memory, and I/O, our fourth post zoomed in on communication patterns. Because at Riptides, communication isn’t just performance data-it’s identity data.
Our eBPF-based pipeline captures how services behave when they initiate or receive connections. What identities they use. Whether they comply with policy. If they retry, escalate, or fail silently. These behaviors form a behavioral fingerprint.
By combining this with identity protocols like SPIFFE and enforcing policy through in kernel controls (like kTLS and in kernel mTLS), we don’t just observe; we enforce trust at the lowest possible level.

Why Metrics Matter for Non-Human Identity
In human-centric security, we rely on context: location, device, login history. For workloads, the kernel is that context.
- Did this pod establish mTLS with a peer inside the cluster or across a boundary?
- Is this service making calls outside its declared dependency graph?
- Was this binary spawned by a known parent process, or was it injected?
These are kernel-level questions. And their answers emerge from kernel level metrics.
That’s why we anchored our non-human identity platform in Linux telemetry. Metrics aren’t just a monitoring tool-they’re a source of truth. They let us prove that identity isn’t just declared, but expressed in how code behaves.
Conclusion: Identity, Observability, and the Kernel
Security starts with identity-but trust is built on behavior. At Riptides, we use Linux telemetry to tie identity to behavior in real-time, without relying on user-space agents or guesswork.
By tracing from the kernel up, we deliver deep observability and robust non-human identity enforcement that scales across clusters, clouds, and container runtimes.
The kernel is speaking. We're just making sure the right systems are listening.
Ready to replace secrets
with trusted identities?
Build with trust at the core.
